mirror of
https://github.com/springzfx/cgproxy.git
synced 2026-02-09 21:14:57 +08:00
Compare commits
6 Commits
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
5c16fdfb9f | ||
|
|
f55b09ec12 | ||
|
|
6ae12bf5c4 | ||
|
|
31627dd956 | ||
|
|
9f8d540c78 | ||
|
|
b8204126c5 |
2
.gitignore
vendored
2
.gitignore
vendored
@@ -1,3 +1,5 @@
|
|||||||
build
|
build
|
||||||
.directory
|
.directory
|
||||||
.vscode
|
.vscode
|
||||||
|
v2ray_config/proxy
|
||||||
|
v2ray_config/06_outbounds_proxy.json
|
||||||
|
|||||||
@@ -1,6 +1,6 @@
|
|||||||
cmake_minimum_required(VERSION 3.10)
|
cmake_minimum_required(VERSION 3.10)
|
||||||
|
|
||||||
project(cgproxy VERSION 3.4)
|
project(cgproxy VERSION 3.5)
|
||||||
add_executable(cgattach cgattach.cpp)
|
add_executable(cgattach cgattach.cpp)
|
||||||
|
|
||||||
install(TARGETS cgattach DESTINATION /usr/bin
|
install(TARGETS cgattach DESTINATION /usr/bin
|
||||||
@@ -23,11 +23,12 @@ install(FILES cgroup-tproxy.sh
|
|||||||
DESTINATION /usr/share/cgproxy/scripts/)
|
DESTINATION /usr/share/cgproxy/scripts/)
|
||||||
|
|
||||||
|
|
||||||
## deb pack
|
## package for deb and rpm
|
||||||
set(CPACK_GENERATOR "DEB;RPM")
|
set(CPACK_GENERATOR "DEB;RPM")
|
||||||
set(CPACK_PACKAGE_NAME "cgproxy")
|
set(CPACK_PACKAGE_NAME "cgproxy")
|
||||||
set(CPACK_PACKAGE_DESCRIPTION_SUMMARY "cgproxy will transparent proxy anything running in specific cgroup.It aslo supports global transparent proxy and gateway proxy")
|
set(CPACK_PACKAGE_DESCRIPTION_SUMMARY "cgproxy will transparent proxy anything running in specific cgroup.It aslo supports global transparent proxy and gateway proxy")
|
||||||
|
|
||||||
|
## deb pack
|
||||||
set(CPACK_DEBIAN_PACKAGE_NAME "cgproxy")
|
set(CPACK_DEBIAN_PACKAGE_NAME "cgproxy")
|
||||||
set(CPACK_DEBIAN_PACKAGE_ARCHITECTURE "x86_64")
|
set(CPACK_DEBIAN_PACKAGE_ARCHITECTURE "x86_64")
|
||||||
set(CPACK_DEBIAN_PACKAGE_DEPENDS "systemd")
|
set(CPACK_DEBIAN_PACKAGE_DEPENDS "systemd")
|
||||||
@@ -38,10 +39,12 @@ set(CPACK_DEBIAN_PACKAGE_MAINTAINER "springzfx@gmail.com")
|
|||||||
set(CONTROL_DIR ${CMAKE_SOURCE_DIR}/control)
|
set(CONTROL_DIR ${CMAKE_SOURCE_DIR}/control)
|
||||||
set(CPACK_DEBIAN_PACKAGE_CONTROL_EXTRA "${CONTROL_DIR}/postinst;${CONTROL_DIR}/prerm")
|
set(CPACK_DEBIAN_PACKAGE_CONTROL_EXTRA "${CONTROL_DIR}/postinst;${CONTROL_DIR}/prerm")
|
||||||
|
|
||||||
|
## rpm pack
|
||||||
set(CPACK_RPM_PACKAGE_ARCHITECTURE, "x86_64")
|
set(CPACK_RPM_PACKAGE_ARCHITECTURE, "x86_64")
|
||||||
set(CPACK_RPM_PACKAGE_REQUIRES "systemd")
|
set(CPACK_RPM_PACKAGE_REQUIRES "systemd")
|
||||||
set(CPACK_RPM_PACKAGE_GROUP "network")
|
set(CPACK_RPM_PACKAGE_GROUP "network")
|
||||||
set(CPACK_RPM_PACKAGE_URL "https://github.com/springzfx/cgproxy")
|
set(CPACK_RPM_PACKAGE_URL "https://github.com/springzfx/cgproxy")
|
||||||
|
set(CONTROL_DIR ${CMAKE_SOURCE_DIR}/control)
|
||||||
set(CPACK_RPM_POST_INSTALL_SCRIPT_FILE "${CONTROL_DIR}/postinst")
|
set(CPACK_RPM_POST_INSTALL_SCRIPT_FILE "${CONTROL_DIR}/postinst")
|
||||||
set(CPACK_RPM_PRE_UNINSTALL_SCRIPT_FILE "${CONTROL_DIR}/prerm")
|
set(CPACK_RPM_PRE_UNINSTALL_SCRIPT_FILE "${CONTROL_DIR}/prerm")
|
||||||
|
|
||||||
|
|||||||
@@ -5,8 +5,9 @@
|
|||||||
## cgroup transparent proxy
|
## cgroup transparent proxy
|
||||||
## any process in cgroup_proxy will be proxied, and cgroup_noproxy the opposite
|
## any process in cgroup_proxy will be proxied, and cgroup_noproxy the opposite
|
||||||
## cgroup must start with slash '/'
|
## cgroup must start with slash '/'
|
||||||
# cgroup_proxy="/"
|
# cgroup_proxy="/"
|
||||||
cgroup_proxy="/proxy.slice"
|
cgroup_proxy="/proxy.slice"
|
||||||
|
# cgroup_noproxy="/system.slice/v2ray.service"
|
||||||
cgroup_noproxy="/noproxy.slice"
|
cgroup_noproxy="/noproxy.slice"
|
||||||
|
|
||||||
########################################################################
|
########################################################################
|
||||||
@@ -28,6 +29,6 @@ enable_dns=true
|
|||||||
########################################################################
|
########################################################################
|
||||||
## do not modify this if you don't known what you are doing
|
## do not modify this if you don't known what you are doing
|
||||||
table=100
|
table=100
|
||||||
mark_proxy=0x01
|
fwmark=0x01
|
||||||
mark_noproxy=0xff
|
mark_noproxy=0xff
|
||||||
mark_newin=0x02
|
mark_newin=0x02
|
||||||
@@ -47,7 +47,7 @@ enable_dns=true
|
|||||||
|
|
||||||
## do not modify this if you don't known what you are doing
|
## do not modify this if you don't known what you are doing
|
||||||
table=100
|
table=100
|
||||||
mark_proxy=0x01
|
fwmark=0x01
|
||||||
mark_noproxy=0xff
|
mark_noproxy=0xff
|
||||||
make_newin=0x02
|
make_newin=0x02
|
||||||
|
|
||||||
@@ -79,13 +79,13 @@ case $i in
|
|||||||
ip6tables -t mangle -X TPROXY_PRE
|
ip6tables -t mangle -X TPROXY_PRE
|
||||||
ip6tables -t mangle -X TPROXY_OUT
|
ip6tables -t mangle -X TPROXY_OUT
|
||||||
ip6tables -t mangle -X TPROXY_ENT
|
ip6tables -t mangle -X TPROXY_ENT
|
||||||
ip rule delete fwmark $mark_proxy lookup $table
|
ip rule delete fwmark $fwmark lookup $table
|
||||||
ip route flush table $table
|
ip route flush table $table
|
||||||
ip -6 rule delete fwmark $mark_proxy lookup $table
|
ip -6 rule delete fwmark $fwmark lookup $table
|
||||||
ip -6 route flush table $table
|
ip -6 route flush table $table
|
||||||
## may not exist, just ignore, and tracking their existence is reliable
|
## may not exist, just ignore, and tracking their existence is not reliable
|
||||||
iptables -t nat -D POSTROUTING -m addrtype ! --src-type LOCAL -j MASQUERADE &> /dev/null
|
iptables -t nat -D POSTROUTING -m owner ! --socket-exists -j MASQUERADE &> /dev/null
|
||||||
ip6tables -t nat -D POSTROUTING -m addrtype ! --src-type LOCAL -j MASQUERADE &> /dev/null
|
ip6tables -t nat -D POSTROUTING -m owner ! --socket-exists -j MASQUERADE &> /dev/null
|
||||||
exit 0
|
exit 0
|
||||||
;;
|
;;
|
||||||
--config=*)
|
--config=*)
|
||||||
@@ -106,16 +106,18 @@ test -d $cgroup_mount_point$cgroup_noproxy || mkdir $cgroup_mount_point$cgroup_
|
|||||||
|
|
||||||
## use TPROXY
|
## use TPROXY
|
||||||
#ipv4#
|
#ipv4#
|
||||||
ip rule add fwmark $mark_proxy table $table
|
ip rule add fwmark $fwmark table $table
|
||||||
ip route add local default dev lo table $table
|
ip route add local default dev lo table $table
|
||||||
iptables -t mangle -N TPROXY_ENT
|
iptables -t mangle -N TPROXY_ENT
|
||||||
iptables -t mangle -A TPROXY_ENT -p tcp -j TPROXY --on-ip 127.0.0.1 --on-port $port --tproxy-mark $mark_proxy
|
iptables -t mangle -A TPROXY_ENT -p tcp -j TPROXY --on-ip 127.0.0.1 --on-port $port --tproxy-mark $fwmark
|
||||||
iptables -t mangle -A TPROXY_ENT -p udp -j TPROXY --on-ip 127.0.0.1 --on-port $port --tproxy-mark $mark_proxy
|
iptables -t mangle -A TPROXY_ENT -p udp -j TPROXY --on-ip 127.0.0.1 --on-port $port --tproxy-mark $fwmark
|
||||||
|
|
||||||
iptables -t mangle -N TPROXY_PRE
|
iptables -t mangle -N TPROXY_PRE
|
||||||
|
iptables -t mangle -A TPROXY_PRE -m socket --transparent -j MARK --set-mark $fwmark
|
||||||
|
iptables -t mangle -A TPROXY_PRE -m socket --transparent -j RETURN
|
||||||
|
iptables -t mangle -A TPROXY_PRE -p icmp -j RETURN
|
||||||
iptables -t mangle -A TPROXY_PRE -p udp --dport 53 -j TPROXY_ENT
|
iptables -t mangle -A TPROXY_PRE -p udp --dport 53 -j TPROXY_ENT
|
||||||
iptables -t mangle -A TPROXY_PRE -p tcp --dport 53 -j TPROXY_ENT
|
iptables -t mangle -A TPROXY_PRE -p tcp --dport 53 -j TPROXY_ENT
|
||||||
iptables -t mangle -A TPROXY_PRE -p icmp -j RETURN
|
|
||||||
iptables -t mangle -A TPROXY_PRE -m addrtype --dst-type LOCAL -j RETURN
|
iptables -t mangle -A TPROXY_PRE -m addrtype --dst-type LOCAL -j RETURN
|
||||||
iptables -t mangle -A TPROXY_PRE -m pkttype --pkt-type broadcast -j RETURN
|
iptables -t mangle -A TPROXY_PRE -m pkttype --pkt-type broadcast -j RETURN
|
||||||
iptables -t mangle -A TPROXY_PRE -m pkttype --pkt-type multicast -j RETURN
|
iptables -t mangle -A TPROXY_PRE -m pkttype --pkt-type multicast -j RETURN
|
||||||
@@ -126,22 +128,26 @@ iptables -t mangle -N TPROXY_OUT
|
|||||||
iptables -t mangle -A TPROXY_OUT -o lo -j RETURN
|
iptables -t mangle -A TPROXY_OUT -o lo -j RETURN
|
||||||
iptables -t mangle -A TPROXY_OUT -p icmp -j RETURN
|
iptables -t mangle -A TPROXY_OUT -p icmp -j RETURN
|
||||||
iptables -t mangle -A TPROXY_OUT -m connmark --mark $make_newin -j RETURN
|
iptables -t mangle -A TPROXY_OUT -m connmark --mark $make_newin -j RETURN
|
||||||
|
iptables -t mangle -A TPROXY_OUT -m pkttype --pkt-type broadcast -j RETURN
|
||||||
|
iptables -t mangle -A TPROXY_OUT -m pkttype --pkt-type multicast -j RETURN
|
||||||
iptables -t mangle -A TPROXY_OUT -m mark --mark $mark_noproxy -j RETURN
|
iptables -t mangle -A TPROXY_OUT -m mark --mark $mark_noproxy -j RETURN
|
||||||
iptables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_noproxy -j RETURN
|
iptables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_noproxy -j RETURN
|
||||||
iptables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_proxy -j MARK --set-mark $mark_proxy
|
iptables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_proxy -j MARK --set-mark $fwmark
|
||||||
iptables -t mangle -A OUTPUT -j TPROXY_OUT
|
iptables -t mangle -A OUTPUT -j TPROXY_OUT
|
||||||
|
|
||||||
#ipv6#
|
#ipv6#
|
||||||
ip -6 rule add fwmark $mark_proxy table $table
|
ip -6 rule add fwmark $fwmark table $table
|
||||||
ip -6 route add local default dev lo table $table
|
ip -6 route add local default dev lo table $table
|
||||||
ip6tables -t mangle -N TPROXY_ENT
|
ip6tables -t mangle -N TPROXY_ENT
|
||||||
ip6tables -t mangle -A TPROXY_ENT -p tcp -j TPROXY --on-ip ::1 --on-port $port --tproxy-mark $mark_proxy
|
ip6tables -t mangle -A TPROXY_ENT -p tcp -j TPROXY --on-ip ::1 --on-port $port --tproxy-mark $fwmark
|
||||||
ip6tables -t mangle -A TPROXY_ENT -p udp -j TPROXY --on-ip ::1 --on-port $port --tproxy-mark $mark_proxy
|
ip6tables -t mangle -A TPROXY_ENT -p udp -j TPROXY --on-ip ::1 --on-port $port --tproxy-mark $fwmark
|
||||||
|
|
||||||
ip6tables -t mangle -N TPROXY_PRE
|
ip6tables -t mangle -N TPROXY_PRE
|
||||||
|
ip6tables -t mangle -A TPROXY_PRE -m socket --transparent -j MARK --set-mark $fwmark
|
||||||
|
ip6tables -t mangle -A TPROXY_PRE -m socket --transparent -j RETURN
|
||||||
|
ip6tables -t mangle -A TPROXY_PRE -p icmp -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_PRE -p udp --dport 53 -j TPROXY_ENT
|
ip6tables -t mangle -A TPROXY_PRE -p udp --dport 53 -j TPROXY_ENT
|
||||||
ip6tables -t mangle -A TPROXY_PRE -p tcp --dport 53 -j TPROXY_ENT
|
ip6tables -t mangle -A TPROXY_PRE -p tcp --dport 53 -j TPROXY_ENT
|
||||||
ip6tables -t mangle -A TPROXY_PRE -p icmp -j RETURN
|
|
||||||
ip6tables -t mangle -A TPROXY_PRE -m addrtype --dst-type LOCAL -j RETURN
|
ip6tables -t mangle -A TPROXY_PRE -m addrtype --dst-type LOCAL -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_PRE -m pkttype --pkt-type broadcast -j RETURN
|
ip6tables -t mangle -A TPROXY_PRE -m pkttype --pkt-type broadcast -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_PRE -m pkttype --pkt-type multicast -j RETURN
|
ip6tables -t mangle -A TPROXY_PRE -m pkttype --pkt-type multicast -j RETURN
|
||||||
@@ -151,10 +157,12 @@ ip6tables -t mangle -A PREROUTING -j TPROXY_PRE
|
|||||||
ip6tables -t mangle -N TPROXY_OUT
|
ip6tables -t mangle -N TPROXY_OUT
|
||||||
ip6tables -t mangle -A TPROXY_OUT -o lo -j RETURN
|
ip6tables -t mangle -A TPROXY_OUT -o lo -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_OUT -p icmp -j RETURN
|
ip6tables -t mangle -A TPROXY_OUT -p icmp -j RETURN
|
||||||
|
ip6tables -t mangle -A TPROXY_OUT -m pkttype --pkt-type broadcast -j RETURN
|
||||||
|
ip6tables -t mangle -A TPROXY_OUT -m pkttype --pkt-type multicast -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_OUT -m connmark --mark $make_newin -j RETURN
|
ip6tables -t mangle -A TPROXY_OUT -m connmark --mark $make_newin -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_OUT -m mark --mark $mark_noproxy -j RETURN
|
ip6tables -t mangle -A TPROXY_OUT -m mark --mark $mark_noproxy -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_noproxy -j RETURN
|
ip6tables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_noproxy -j RETURN
|
||||||
ip6tables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_proxy -j MARK --set-mark $mark_proxy
|
ip6tables -t mangle -A TPROXY_OUT -m cgroup --path $cgroup_proxy -j MARK --set-mark $fwmark
|
||||||
ip6tables -t mangle -A OUTPUT -j TPROXY_OUT
|
ip6tables -t mangle -A OUTPUT -j TPROXY_OUT
|
||||||
|
|
||||||
## allow to disable, order is important
|
## allow to disable, order is important
|
||||||
@@ -189,13 +197,14 @@ ip6tables -t mangle -I TPROXY_PRE -m addrtype ! --src-type LOCAL -m conntrack --
|
|||||||
|
|
||||||
## message for user
|
## message for user
|
||||||
cat << DOC
|
cat << DOC
|
||||||
|
noproxy cgroup: $cgroup_noproxy
|
||||||
proxied cgroup: $cgroup_proxy
|
proxied cgroup: $cgroup_proxy
|
||||||
DOC
|
DOC
|
||||||
|
|
||||||
|
|
||||||
if $enable_gateway; then
|
if $enable_gateway; then
|
||||||
iptables -t nat -A POSTROUTING -m addrtype ! --src-type LOCAL -j MASQUERADE
|
iptables -t nat -A POSTROUTING -m owner ! --socket-exists -j MASQUERADE
|
||||||
ip6tables -t nat -A POSTROUTING -m addrtype ! --src-type LOCAL -j MASQUERADE
|
ip6tables -t nat -A POSTROUTING -m owner ! --socket-exists -j MASQUERADE
|
||||||
sysctl -w net.ipv4.ip_forward=1
|
sysctl -w net.ipv4.ip_forward=1
|
||||||
sysctl -w net.ipv6.conf.all.forwarding=1
|
sysctl -w net.ipv6.conf.all.forwarding=1
|
||||||
echo "gateway enabled"
|
echo "gateway enabled"
|
||||||
|
|||||||
24
readme.md
24
readme.md
@@ -44,7 +44,9 @@ It aslo supports global transparent proxy and gateway proxy. See [Global transpa
|
|||||||
mkdir build && cd build && cmake .. && make && make install
|
mkdir build && cd build && cmake .. && make && make install
|
||||||
```
|
```
|
||||||
|
|
||||||
It is alreay in [archlinux AUR](https://aur.archlinux.org/packages/cgproxy/).
|
- It is alreay in [archlinux AUR](https://aur.archlinux.org/packages/cgproxy/).
|
||||||
|
|
||||||
|
- DEB and RPM are packaged in [release page](https://github.com/springzfx/cgproxy/releases).
|
||||||
|
|
||||||
## How to use
|
## How to use
|
||||||
|
|
||||||
@@ -71,14 +73,12 @@ It is alreay in [archlinux AUR](https://aur.archlinux.org/packages/cgproxy/).
|
|||||||
<summary>More config in `/etc/cgproxy.conf` (click to expand)</summary>
|
<summary>More config in `/etc/cgproxy.conf` (click to expand)</summary>
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
# see how to configure
|
|
||||||
# https://github.com/springzfx/cgproxy
|
|
||||||
########################################################################
|
########################################################################
|
||||||
## cgroup transparent proxy
|
## cgroup transparent proxy
|
||||||
## any process in cgroup_proxy will be proxied, and cgroup_noproxy the opposite
|
## any process in cgroup_proxy will be proxied, and cgroup_noproxy the opposite
|
||||||
## cgroup must start with slash '/'
|
## cgroup must start with slash '/'
|
||||||
# cgroup_proxy="/"
|
# cgroup_proxy="/"
|
||||||
cgroup_proxy="/proxy.slice"
|
cgroup_proxy="/proxy.slice"
|
||||||
cgroup_noproxy="/noproxy.slice"
|
cgroup_noproxy="/noproxy.slice"
|
||||||
|
|
||||||
########################################################################
|
########################################################################
|
||||||
@@ -100,7 +100,7 @@ enable_dns=true
|
|||||||
########################################################################
|
########################################################################
|
||||||
## do not modify this if you don't known what you are doing
|
## do not modify this if you don't known what you are doing
|
||||||
table=100
|
table=100
|
||||||
mark_proxy=0x01
|
fwmark=0x01
|
||||||
mark_noproxy=0xff
|
mark_noproxy=0xff
|
||||||
mark_newin=0x02
|
mark_newin=0x02
|
||||||
```
|
```
|
||||||
@@ -129,8 +129,9 @@ sudo systemctl restart cgproxy.service
|
|||||||
|
|
||||||
## Gateway proxy
|
## Gateway proxy
|
||||||
|
|
||||||
- set **enable_gateway=true** in `/etc/cgproxy.conf` and restart service
|
- Set **enable_gateway=true** in `/etc/cgproxy.conf` and restart service
|
||||||
- other device set this host as gateway, and set public dns if necessary
|
- Run your proxy software in cgroup_noproxy to allow direct to internet as above. This is necessary when you use global transparent proxy the same time.
|
||||||
|
- Other device set this host as gateway, and set public dns if necessary
|
||||||
|
|
||||||
## Other useful tools provided in this project
|
## Other useful tools provided in this project
|
||||||
|
|
||||||
@@ -166,9 +167,16 @@ sudo systemctl restart cgproxy.service
|
|||||||
sudo setcap "cap_net_admin,cap_net_bind_service=ep" /usr/lib/v2ray/v2ray
|
sudo setcap "cap_net_admin,cap_net_bind_service=ep" /usr/lib/v2ray/v2ray
|
||||||
```
|
```
|
||||||
|
|
||||||
|
- Why not outbound mark solution, because in v2ray [when `"localhost"` is used, out-going DNS traffic is not controlled by V2Ray](https://www.v2fly.org/en/configuration/dns.html), so no mark at all, that's pitty.
|
||||||
|
|
||||||
## TIPS
|
## TIPS
|
||||||
|
|
||||||
- `systemd-cgls` to see the cgroup hierarchical tree.
|
- `systemd-cgls` to see the cgroup hierarchical tree.
|
||||||
|
- v2ray full config exmaple in [v2ray_buid](https://github.com/springzfx/cgproxy/tree/master/v2ray_buid), more to see [v2ray multi-file config](https://www.v2fly.org/chapter_02/multiple_config.html)
|
||||||
|
- Qv2ray config example
|
||||||
|
|
||||||
|
|
||||||
|
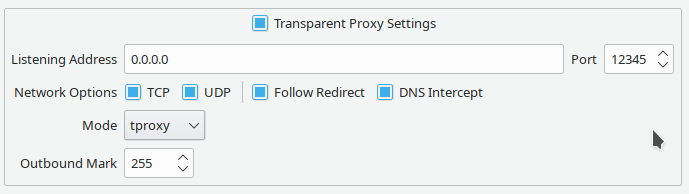
|
||||||
|
|
||||||
## Licences
|
## Licences
|
||||||
|
|
||||||
|
|||||||
5
v2ray_config/00_log.json
Normal file
5
v2ray_config/00_log.json
Normal file
@@ -0,0 +1,5 @@
|
|||||||
|
{
|
||||||
|
"log": {
|
||||||
|
"loglevel": "debug"
|
||||||
|
}
|
||||||
|
}
|
||||||
10
v2ray_config/01_api.json
Normal file
10
v2ray_config/01_api.json
Normal file
@@ -0,0 +1,10 @@
|
|||||||
|
{
|
||||||
|
"api": {
|
||||||
|
"services": [
|
||||||
|
"HandlerService",
|
||||||
|
"LoggerService",
|
||||||
|
"StatsService"
|
||||||
|
],
|
||||||
|
"tag": "API"
|
||||||
|
}
|
||||||
|
}
|
||||||
19
v2ray_config/02_dns.json
Normal file
19
v2ray_config/02_dns.json
Normal file
@@ -0,0 +1,19 @@
|
|||||||
|
{
|
||||||
|
"dns": {
|
||||||
|
"servers": [
|
||||||
|
{
|
||||||
|
"address": "localhost",
|
||||||
|
"port": 53,
|
||||||
|
"domains": [
|
||||||
|
"geosite:cn"
|
||||||
|
],
|
||||||
|
"expectIPs": [
|
||||||
|
"geoip:cn"
|
||||||
|
]
|
||||||
|
},
|
||||||
|
"https+local://1.1.1.1/dns-query",
|
||||||
|
"223.6.6.6"
|
||||||
|
],
|
||||||
|
"tag": "dns_inbound"
|
||||||
|
}
|
||||||
|
}
|
||||||
60
v2ray_config/03_routing.json
Normal file
60
v2ray_config/03_routing.json
Normal file
@@ -0,0 +1,60 @@
|
|||||||
|
{
|
||||||
|
"routing": {
|
||||||
|
"domainStrategy": "IPIfNonMatch",
|
||||||
|
"rules": [
|
||||||
|
{
|
||||||
|
"outboundTag": "dns-out",
|
||||||
|
"port": "53",
|
||||||
|
"type": "field"
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"domain": [
|
||||||
|
"geosite:google",
|
||||||
|
"geosite:github",
|
||||||
|
"geosite:netflix",
|
||||||
|
"geosite:steam",
|
||||||
|
"geosite:telegram",
|
||||||
|
"geosite:tumblr",
|
||||||
|
"geosite:bbc"
|
||||||
|
],
|
||||||
|
"outboundTag": "outBound_PROXY",
|
||||||
|
"type": "field"
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"ip": [
|
||||||
|
"geoip:private"
|
||||||
|
],
|
||||||
|
"outboundTag": "outBound_DIRECT",
|
||||||
|
"type": "field"
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"domain": [
|
||||||
|
"geosite:category-ads-all"
|
||||||
|
],
|
||||||
|
"outboundTag": "outBound_BLACKHOLE",
|
||||||
|
"type": "field"
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"ip": [
|
||||||
|
"geoip:cn"
|
||||||
|
],
|
||||||
|
"outboundTag": "outBound_DIRECT",
|
||||||
|
"type": "field"
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"domain": [
|
||||||
|
"geosite:cn"
|
||||||
|
],
|
||||||
|
"outboundTag": "outBound_DIRECT",
|
||||||
|
"type": "field"
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"inboundTag": [
|
||||||
|
"inbound_API"
|
||||||
|
],
|
||||||
|
"outboundTag": "API",
|
||||||
|
"type": "field"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
|
}
|
||||||
8
v2ray_config/04_policy.json
Normal file
8
v2ray_config/04_policy.json
Normal file
@@ -0,0 +1,8 @@
|
|||||||
|
{
|
||||||
|
"policy": {
|
||||||
|
"system": {
|
||||||
|
"statsInboundDownlink": true,
|
||||||
|
"statsInboundUplink": true
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
14
v2ray_config/05_inbounds_api.json
Normal file
14
v2ray_config/05_inbounds_api.json
Normal file
@@ -0,0 +1,14 @@
|
|||||||
|
{
|
||||||
|
"inbounds": [
|
||||||
|
{
|
||||||
|
"listen": "127.0.0.1",
|
||||||
|
"port": 15490,
|
||||||
|
"protocol": "dokodemo-door",
|
||||||
|
"settings": {
|
||||||
|
"address": "127.0.0.1"
|
||||||
|
},
|
||||||
|
"sniffing": {},
|
||||||
|
"tag": "inbound_API"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
13
v2ray_config/05_inbounds_http.json
Normal file
13
v2ray_config/05_inbounds_http.json
Normal file
@@ -0,0 +1,13 @@
|
|||||||
|
{
|
||||||
|
"inbounds": [
|
||||||
|
{
|
||||||
|
"listen": "127.0.0.1",
|
||||||
|
"port": 8888,
|
||||||
|
"protocol": "http",
|
||||||
|
"sniffing": {
|
||||||
|
"enabled": false
|
||||||
|
},
|
||||||
|
"tag": "http_IN"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
17
v2ray_config/05_inbounds_socks5.json
Normal file
17
v2ray_config/05_inbounds_socks5.json
Normal file
@@ -0,0 +1,17 @@
|
|||||||
|
{
|
||||||
|
"inbounds": [
|
||||||
|
{
|
||||||
|
"listen": "127.0.0.1",
|
||||||
|
"port": 1080,
|
||||||
|
"protocol": "socks",
|
||||||
|
"settings": {
|
||||||
|
"auth": "noauth",
|
||||||
|
"userLevel": 0
|
||||||
|
},
|
||||||
|
"sniffing": {
|
||||||
|
"enabled": false
|
||||||
|
},
|
||||||
|
"tag": "socks_IN"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
30
v2ray_config/05_inbounds_tproxy.json
Normal file
30
v2ray_config/05_inbounds_tproxy.json
Normal file
@@ -0,0 +1,30 @@
|
|||||||
|
{
|
||||||
|
"inbounds": [
|
||||||
|
{
|
||||||
|
"listen": "0.0.0.0",
|
||||||
|
"port": 12345,
|
||||||
|
"protocol": "dokodemo-door",
|
||||||
|
"settings": {
|
||||||
|
"address": "",
|
||||||
|
"followRedirect": true,
|
||||||
|
"network": "tcp,udp",
|
||||||
|
"port": 0,
|
||||||
|
"timeout": 0,
|
||||||
|
"userLevel": 0
|
||||||
|
},
|
||||||
|
"sniffing": {
|
||||||
|
"destOverride": [
|
||||||
|
"http",
|
||||||
|
"tls"
|
||||||
|
],
|
||||||
|
"enabled": true
|
||||||
|
},
|
||||||
|
"streamSettings": {
|
||||||
|
"sockopt": {
|
||||||
|
"tproxy": "tproxy"
|
||||||
|
}
|
||||||
|
},
|
||||||
|
"tag": "tproxy_IN"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
19
v2ray_config/06_outbounds_blackhole.json
Normal file
19
v2ray_config/06_outbounds_blackhole.json
Normal file
@@ -0,0 +1,19 @@
|
|||||||
|
{
|
||||||
|
"outbounds": [
|
||||||
|
{
|
||||||
|
"protocol": "blackhole",
|
||||||
|
"sendThrough": "0.0.0.0",
|
||||||
|
"settings": {
|
||||||
|
"response": {
|
||||||
|
"type": "none"
|
||||||
|
}
|
||||||
|
},
|
||||||
|
"streamSettings": {
|
||||||
|
"sockopt": {
|
||||||
|
"mark": 255
|
||||||
|
}
|
||||||
|
},
|
||||||
|
"tag": "outBound_BLACKHOLE"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
13
v2ray_config/06_outbounds_dns.json
Normal file
13
v2ray_config/06_outbounds_dns.json
Normal file
@@ -0,0 +1,13 @@
|
|||||||
|
{
|
||||||
|
"outbounds": [
|
||||||
|
{
|
||||||
|
"protocol": "dns",
|
||||||
|
"streamSettings": {
|
||||||
|
"sockopt": {
|
||||||
|
"mark": 255
|
||||||
|
}
|
||||||
|
},
|
||||||
|
"tag": "dns-out"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
19
v2ray_config/06_outbounds_freedom.json
Normal file
19
v2ray_config/06_outbounds_freedom.json
Normal file
@@ -0,0 +1,19 @@
|
|||||||
|
{
|
||||||
|
"outbounds": [
|
||||||
|
{
|
||||||
|
"protocol": "freedom",
|
||||||
|
"sendThrough": "0.0.0.0",
|
||||||
|
"settings": {
|
||||||
|
"domainStrategy": "UseIP",
|
||||||
|
"redirect": ":0",
|
||||||
|
"userLevel": 0
|
||||||
|
},
|
||||||
|
"streamSettings": {
|
||||||
|
"sockopt": {
|
||||||
|
"mark": 255
|
||||||
|
}
|
||||||
|
},
|
||||||
|
"tag": "outBound_DIRECT"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
1
v2ray_config/06_outbounds_myproxy.json
Normal file
1
v2ray_config/06_outbounds_myproxy.json
Normal file
@@ -0,0 +1 @@
|
|||||||
|
{}
|
||||||
1
v2ray_config/07_transport.json
Normal file
1
v2ray_config/07_transport.json
Normal file
@@ -0,0 +1 @@
|
|||||||
|
{}
|
||||||
3
v2ray_config/08_stats.json
Normal file
3
v2ray_config/08_stats.json
Normal file
@@ -0,0 +1,3 @@
|
|||||||
|
{
|
||||||
|
"stats": {}
|
||||||
|
}
|
||||||
1
v2ray_config/09_reverse.json
Normal file
1
v2ray_config/09_reverse.json
Normal file
@@ -0,0 +1 @@
|
|||||||
|
{}
|
||||||
2
v2ray_config/merge.sh
Normal file
2
v2ray_config/merge.sh
Normal file
@@ -0,0 +1,2 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
jq -rs 'reduce .[] as $item ({}; . + $item + {inbounds: (.inbounds + $item.inbounds)} + {outbounds: ($item.outbounds + .outbounds)})' *.json |sudo tee /etc/v2ray/config.json
|
||||||
1
v2ray_config/readme.md
Normal file
1
v2ray_config/readme.md
Normal file
@@ -0,0 +1 @@
|
|||||||
|
Fill `06_outbounds_myproxy.json` with your vmess proxy config with tag `outBound_PROXY`.
|
||||||
19
v2ray_config/v2ray.service
Normal file
19
v2ray_config/v2ray.service
Normal file
@@ -0,0 +1,19 @@
|
|||||||
|
[Unit]
|
||||||
|
Description=V2Ray - A unified platform for anti-censorship
|
||||||
|
Documentation=https://v2ray.com https://guide.v2fly.org
|
||||||
|
After=network.target nss-lookup.target
|
||||||
|
Wants=network-online.target
|
||||||
|
|
||||||
|
[Service]
|
||||||
|
Type=simple
|
||||||
|
User=nobody
|
||||||
|
#AmbientCapabilities=CAP_NET_ADMIN CAP_NET_BIND_SERVICE
|
||||||
|
CapabilityBoundingSet=CAP_NET_ADMIN CAP_NET_BIND_SERVICE
|
||||||
|
NoNewPrivileges=yes
|
||||||
|
ExecStart=+/usr/lib/v2ray/v2ray -config /etc/v2ray/config.json
|
||||||
|
Restart=on-failure
|
||||||
|
# Don't restart in the case of configuration error
|
||||||
|
RestartPreventExitStatus=23
|
||||||
|
|
||||||
|
[Install]
|
||||||
|
WantedBy=multi-user.target
|
||||||
Reference in New Issue
Block a user